This was an interesting request that came up on the VMTN community forums asking whether it was possible to block users from accessing the vSphere HTML5 (H5) VM Console in vCenter Server and only allowing access to a VM console through the use of the Standalone VM Remote Console (VMRC) client? What is the use case for this you might ask, well it looks like VM screen resolution was getting change between the two clients and the administrator simply wanted to restrict access to the H5 VM Console and direct users to use only the VMRC Client.
At first, I could not see how this could be accomplished since all of their users already have the "Console interaction" privilege within vCenter Server which allows them to to interact with both VM Console interfaces. I was then reminded of an article that I wrote back in 2021 where a user wanted to restrict access to the vSphere UI interface while still allowing access to vCenter Server through the vSphere API, which used an access policy to restrict access based on a URI endpoint within the vCenter Server Tomcat application configuration.
This gave me an idea to experiment with and see if we could do the same and simply restrict the /ui/vmconsole endpoint which serves the H5 VM Console while still preserving VMRC access.
Step 1 - SSH to vCenter Server Appliance (VCSA) and edit the following /usr/lib/vmware-vsphere-ui/server/conf/web.xml file and append the following security constraint at the bottom of the file right above the closing web-app tag as shown in screenshot below.
<security-constraint>
<web-resource-collection>
<web-resource-name>Restricted</web-resource-name>
<url-pattern>/ui/webconsole.html</url-pattern>
<http-method>GET</http-method>
</web-resource-collection>
<auth-constraint />
</security-constraint>
UPDATE (04/03/2024) - For VCSA 8.0 Update 1 and later, you may need to include the <web-resource-name> tag or vSphere UI service may fail to restart.
Note: If you do not want to completely disable the H5 VM Console, you can also add authentication to this endpoint, for more details see this blog post for more information.
Step 2 - For the change to go into effect, we need to restart the vSphere UI service by running the following command:
service-control --restart vsphere-ui
Once the vSphere UI has been restarted, when attempting to access the H5 VM Console, you will get an HTTP 403 Forbidden message and as you can see from the screenshot but accessing the standalone VMRC is 100% functional 😀
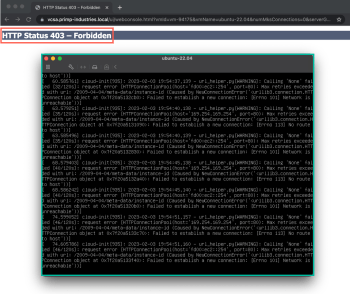
It is good to know that this is possible but probably not something I see being used broadly, especially with the connivence of H5 VM Console and the use of standalone VMRC also requires direct connectivity from the end users desktop to your underlying ESXi infrastructure, unless you enable the new VMRC proxy feature introduced in vSphere 7.x.
Disclaimer: Please be aware that non-default configuration changes may not be officially supported by VMware and more specifically, the original default values may be reverted upon an update and/or upgrade of the VCSA. If you intend to make use of this functionality, you will be responsible to ensure these changes are persisted with future updates.

https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.vm_admin.doc/GUID-239B230C-CE7B-4052-913B-0BAECBA807D5.html There is this option to use vCenter as a proxy for vmrc. So it is not neccessary that Port 443 from managment station to ESX is allowed. If proxy is activated all connection use the proxy. Is it possible to exclude some IP ranges from proxy ?
Ah, good to hear that feature has shipped to on-prem vSphere. I had written about it when it was released in VMware Cloud on AWS https://williamlam.com/2020/12/vmware-cloud-on-aws-1-13-adds-support-for-vmrc-vcenter-proxy.html but had lost track on when it was coming to vSphere on-prem