This past weekend I was finishing up a couple of demo recordings for my VMworld sessions in case the live demos fail for whatever reason, which has happened to me in the past. A few of the demos involve the vSphere Web Client UI and I thought instead of wasting time and potentially fat fingering credentials up on stage, I would try to do everything I can to remove any potential hiccups. In vSphere 6.0, the vCenter Single Sign-On page is now completely in HTML and this not only means you can customize the UI as I have shown here but you can also do some other neat tricks with it.
I decided to update the HTML page to automatically pre-fill both the SSO username and password, so that when I need to login to the vSphere Web Client, I just have to hit the tab key and then click on the login button.
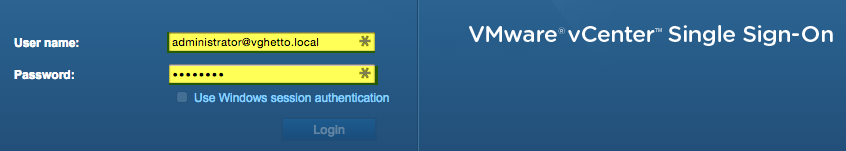
Disclaimer: Outside of a home lab or demo purposes, there is really no good reason for this. I can already hear Mike Foley sighing right now 😉 This also means that anyone who knows the address of your vSphere Web Client can just login, so you may want to only pre-fill the username and still type out the password in case you are concerned with that.
To pre-fill the value for the SSO username and/or password, you will need to edit the following file:
- Windows VC: C:\ProgramData\VMware\vCenterServer\runtime\VMwareSTSService\webapps\websso\WEB-INF\views\unpentry.jsp
- VCSA: /usr/lib/vmware-sso/vmware-sts/webapps/websso/WEB-INF/views/unpentry.jsp
For pre-filling the username, you will need to add a "value" property along with its actual value in the following section:
<input id="username" class="margeTextInput" type="text" value="*protected email*"/>
For pre-filling the password, you will need to add a "value" property along with its actual value in the following section:
<input id="password" class="margeTextInput" type="password" value="VMware1!"/>
Once you have saved your changes, you can then reload the browser and you should see that the vSphere Web Client now has both the username and password automatically pre-filled when the webpage loads.




